Bastion server/Jump Server
Bastion server/Jump Server
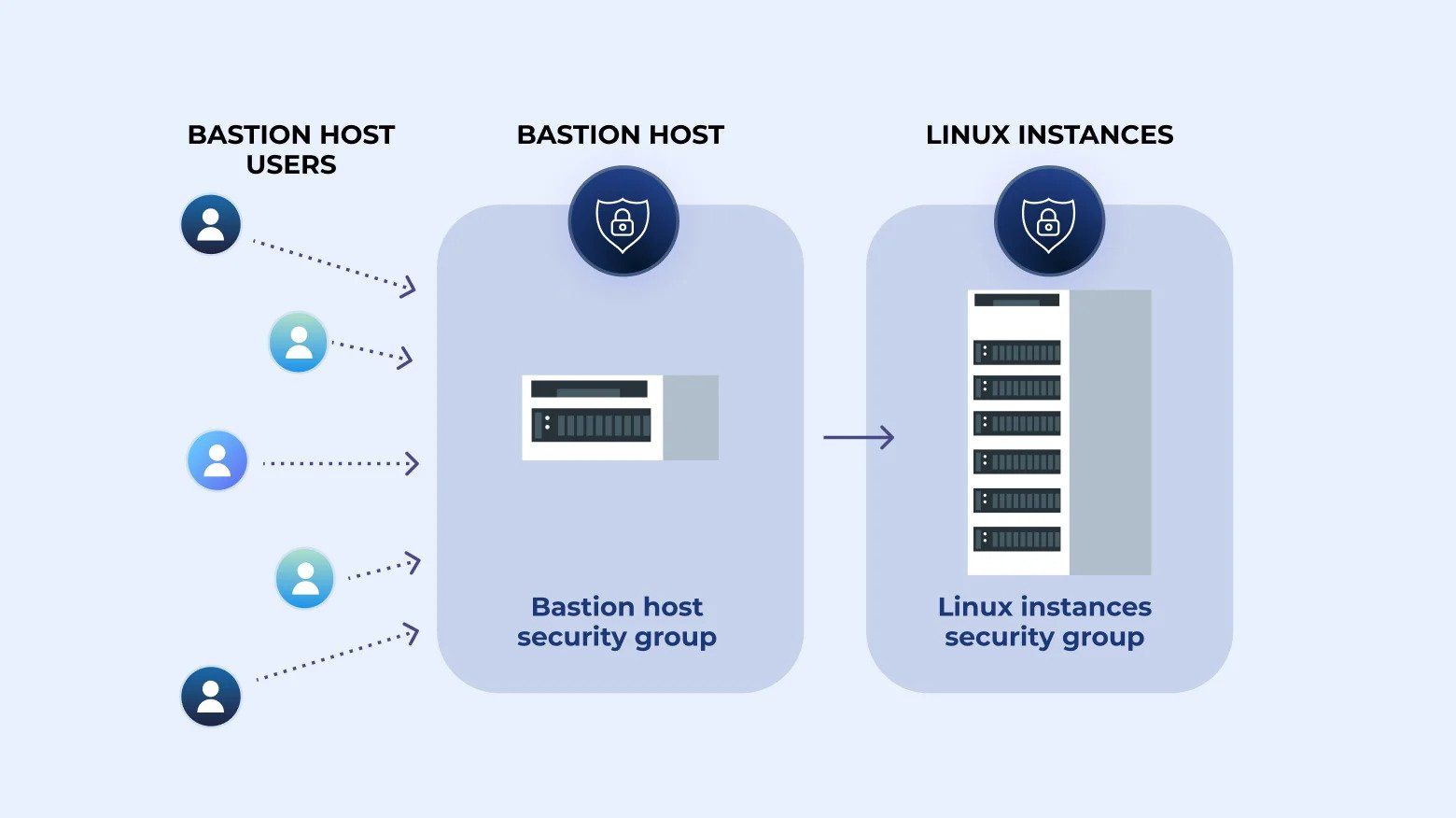
The main purpose of a bastion server: acting as a gateway to access other servers within a network.It's your first line of defense against potential cyber threats.
Imagine your internal servers are a well-guarded castle. The bastion server is like the guarded drawbridge. It controls who gets in and out. This helps keep the important stuff inside the castle safe from any bad guys outside.
By having just one way in (through the bastion), you're reducing the number of doors that attackers can try to open. It's like putting a super-strong lock on that one door. The bastion server takes the hits and keeps the internal servers hidden.
Bastion servers are set up to allow only authorized users to access the internal network. This means that even if a malicious bot or crawler attempts to connect to the network, it won't be able to bypass the bastion server's authentication and access controls.
suppose we have two server first one that will be act as a host 135.180.39.205 while other one our destination server 65.101.111.10
the firewall will have to set for those , first for host you have to disable all port except the port which will be use for ssh, in our case its 5001, so we only allow it.
More on destination server we have to add rule to allow only the bastion server Ip address which is 135.180.39.205.
add this to your ~/.ssh/config , if config file not exits just create it and add below configuration.
Host jump
HostName 135.180.39.205
Port 5001
User root
IdentityFile c:\path\to\privatekey
Host destination_server
HostName 65.101.111.10
Port 40003
User kashif
IdentityFile c:\path\to\privatekey
ProxyJump jump
after above just ssh by
ssh destination_server
more generate key like this
ssh-keygen -t rsa -b 4096
Then on server
~/.ssh/authorized_keys
add your public key there on bastion and destination server to access it
For best practice always follow for bastian server create simple user for others while keep root user for yourself
create other user,then create directory in their path
mkdir -p ~/.ssh
sudo nano authorized_keys
paste their public key content in above
